
Before we begin today’s tech tip, we first wholeheartedly thank all Veterans for their courage and commitment past and present. It is this, that gives us others the opportunity to worry about free society business risks, like the financial risks we describe below. Thank you, from Tech Essentials.
If you’re a Simpsons fan, you may remember a memorable scene in the 2007 movie where a future President Schwarzenegger tells a staffer who presents him with 5 policy briefs that, “I was elected to lead, not to read.” (You need to say this aloud in your best Ahnold accent to get the full effect.)
[Join our email security and eSignature product web briefings next week! Click to register. Or, join our real estate and settlement services session with RESPRO. Click to register.]
Similarly, you may recall that a few weeks ago we covered how some email gateways have alerting capabilities for reply hijacking and anti-whaling, which is, on the surface, a good thing. Who wouldn’t want to know if the email address they are replying to is not the actual email address they expect?
This problem is if these email gateways simply stamp alerts in the subject or first line of literally every inbound email that you receive (e.g., [EXTERNAL] added to the subject, or in red text on the first line ‘Don’t click links in this email unless you trust the sender’), you are then required to have to read each of these alerts very carefully to see if a mismatch in addresses exists. (If it does, you are the potential victim of a whaling Business Email Compromise attack.) You may now have that same Ahnold voice in your head screaming, “I am paid to lead, not to read!”
These email gateways that ‘over alert’ you are effectively the boy who cried wolf, and we all know how that story ends. However, there’s another wrinkle in this email stamp story that I’ve discovered as it pertains to sales/marketing emails: I’m seeing that some recently received marketing emails have their own pre-marked stamp, a total lark that is meant to instill confidence in the email’s provenance. There’s one I got last week that goes as far to have “[EXTERNAL]” in the subject line. NOTE, I don’t have any inbound security gateway that stamps these on, so it was certainly done by the email marketing firm. I can only imagine the A/B tests that were run to determine that the stamped emails have the higher open rates.
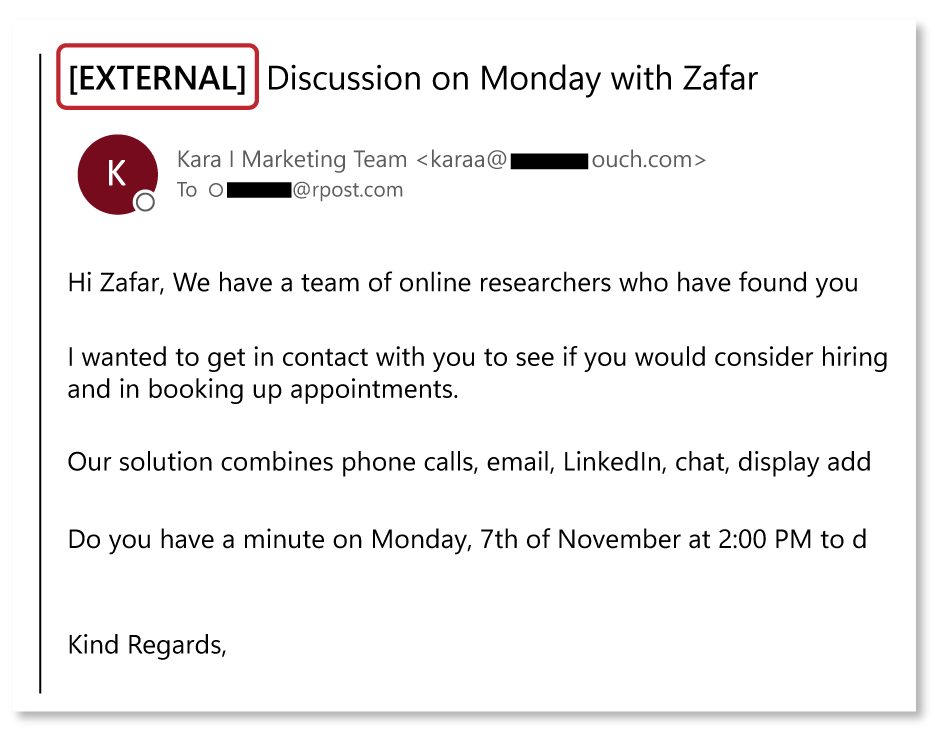
This runs completely counter to the spirit of having gateway alerts in the first place—to warn you NOT to open the email. Now marketers are hoping that these stamps get you to open them as they add an aura of legitimacy to the email. How long will it now take for scammers to seize on this false sense of confidence so as to send BEC emails guised as marketing emails. My bet is that it’s probably happening right now.
As we’ve written in Tech Essentials many times over the past few months, this is precisely why you need RMail’s layered technology approach to defeat BEC attacks — even if you have inbound security buttoned up. Think of RMail as a customer’s very own PRE-Crime™ fighting agency (à la Minority Report). Plus, we promise it won’t bombard you with “cry-wolf” alerts that will lull you into a false sense of security.
In the case discussed above, RMail’s Lookalike Domain detector would be invaluable. It alerts a sender after they click forward, reply or reply all, before the email is sent, if one of the domains in their recipient list is likely a malicious lookalike domain similar to one of their contacts. No wolf crying here!
Some other relevant components of RMail’s PRE-Crime™ service are:
Learn More:
How to Recall an Email in Outlook
Yes, you are paid to lead and not to read (an endless torrent of bogus email security stamps). Imagine the great things you will do once you no longer have to vet email stamp alerts. Please contact us to learn more about RMail’s PRE-Crime™ service and all its cutting edge features.

March 06, 2026

February 27, 2026

February 20, 2026
.jpg)
February 13, 2026

February 06, 2026