Did you know that the United States was the top country for an average total cost of a data breach for the eleventh year in a row?
An IBM security analysis pegs the average total cost of data breaches due to business email compromise as the highest at $5.01 million, followed by phishing ($4.65 million), malicious insiders ($4.61 million), social engineering ($4.47 million), and compromised credentials ($4.37 million). Additionally, it took an average of 212 days to identify a breach in 2021 and an average of 75 days to contain it!
This brings us to the question.
We give you a hint: not secure enough. The above stats show the alarming rate of losses in revenue and reputation to organizations due to data breaches. So, the question you must ask is how secure is your email? Email remains the primary and most critical and convenient means of communication. But it also acts as a major vulnerability for organizations and users.
Hackers often use deceptive messages to entice recipients to share sensitive information, open attachments, or click on hyperlinks with malware installed to gain a backdoor into an enterprise network and obtain valuable company data.
Often, email is the primary source of all ransomware, malware, phishing attacks, and email threats. Let us understand what those are.
Hackers these days are using various sophisticated techniques than traditional phishing emails or the “Nigerian prince” emails of yesteryears to get to your data. We discuss a few common ones here.
This underscores the importance of email security for businesses and adoption of the best practices to protect your critical data.
With security a top concern, it’s a good idea to proactively adopt some best practices.
Sometimes, even after following these and other email security best practices or setting up email policies, your business could fall victim to data breaches. RMail, a global email security solution from RPost, can help you ward off all these threats with its advanced capabilities. Let us deep dive.
The level of sophistication seen in imposter emails is unmatched today, reflecting a deeper understanding of people’s roles and messaging patterns within a target organization. RMail offers several advanced email security functionalities that helps businesses protect against a majority of email attack vectors.
Picture a scenario. Impostors buy passwords from the dark web, hack into the servers, and keep tabs on activities related to high-value transactions or sensitive financial information. They then buy a domain that is very similar to the one that your staff communicates with and send an email to your team with one letter off or flipped off in the domain (e.g., valleyinsurance.com vs. valleyinsrance.com). This tricks the eye and mind because humans tend not to “read” every letter in a word. Your team thinking the email came from a familiar email address responds and there goes your company’s bank routing numbers or any other highly sensitive financial data.
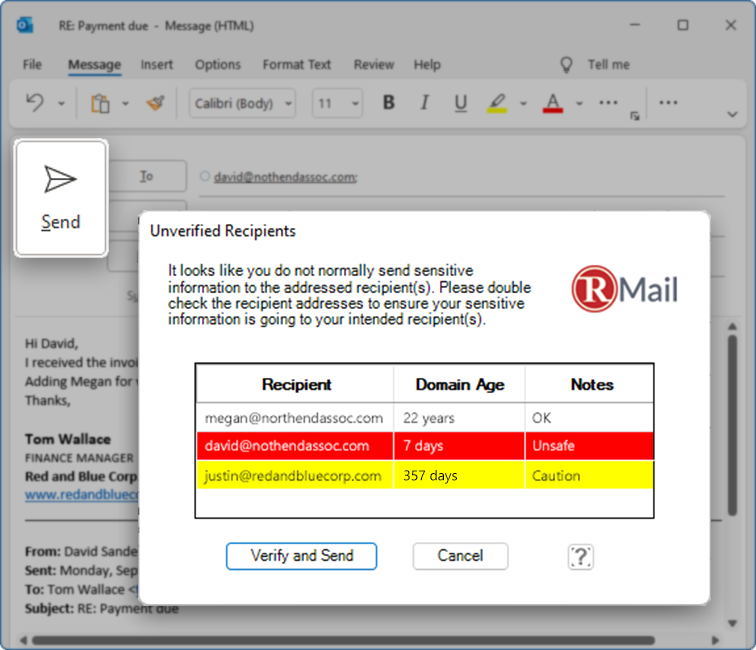
One of the ways RMail prevents such mis-direction of emails is through its advanced “Domain Age Detector” feature, which displays warnings to the sender when they are about to send an email. The recipient “domain age” analysis brings AI into the email-send-flow in real-time. Based on age of the domain, along with other domain metrics, the sender is nudged to pause and re-verify addresses. Relatively new domains are highlighted in yellow or red, as they are more likely to be clever misspells of real addresses and potential threats to email security. You can customize notes and age rules to get alerts on the age of a particular domain.

People forget. Has it ever happened to you that, after sending an email, you regretted not encrypting it as it contained sensitive information or you have completely forgotten to encrypt? This has happened to 35% of the people in the legal sector and almost 70% in the insurance industry. RMail’s advanced “RMail Recommends” feature provides AI-infused and rule-based, in-the-moment e-security and email security training that automatically sensitizes users to treat certain messages differently.
Basically, it reminds you to encrypt your emails when you press the “send” button. So, if you are sending an email that contains a string of characters that look like a SSN or a credit card, for example, RMail will prompt you to suggest or even mandate (depending on your configuration) that you encrypt the email. You can customize the rules. RMail’s AI engine also learns from user behavior and adapts over time.
Have you ever mis-addressed an important email to a wrong person? Most of us have at some time, where we go exclaiming later, “That address sure looked the same!” Such human errors are the number one reason for data breaches and loss of reputation arising out of it. It can be a common mistake or part of a larger cyberattack, where an impostor traps you by creating an email account that looks and reads almost exactly the same as someone in your company. RMail understands the “security of sentiment.”
RMail’s AI engine anticipates email impostor trickery in-the-moment of email interaction. What it does is allow you to pause and prevent such trickery through prompts. If RMail’s AI engine determines that you are about to misaddress a sensitive email, it prompts you to double check the recipient addresses. It also alerts the sender if the recipient domain is likely to be a clever misspell of an authentic recipient domain, considering domain age and other variables (the domain age detector discussed above). This helps ward off those snarky whaling attempts.
In fact, both domain age detector and Right Recipient look at users’ historical message patterns, content, and internet connected intelligence to provide the appropriate (non-intrusive) alerts. The analysis is instant. Once re-verified, you can snooze the alerts for that recipient. You can also tune the frequency and trigger these alerts to your needs.

RMail has an “AI brain” that uses dynamic double-layered email encryption protocols to secure your emails. It adapts smartly per the encryption modes offered by the users’ email clients and switches the email encryption accordingly – without bothering either the sender or the recipient.
1. Transmission level encryption - RMail’s default email encryption mode transmits the message encrypted using a configurable level of TLS or Transport Layer Security and auto decrypts the email messages and attachments for the recipients. Your recipients do not need to enter any password, click any link, or install any software to decrypt the message. The email is sent encrypted right to the recipient’s inbox with a banner that says “Registered Encrypted” email and a text which will tell them that the email was sent encrypted.
2. Message level encryption - If your recipient’s email client does not have TLS or has a lower level of TLS than the minimum TLS threshold, the email will automatically revert to RMail’s “message level” encryption option. It automatically wraps the email content and attachments inside an AES 256-bit encrypted PDF to guarantee 100% email encryption. What this means is that the message and all attachments remain encrypted within the recipient’s email inbox and encapsulated inside a PDF file, and can be read only after decrypting in the recipient’s PDF reader. Here, you can create a password for your recipients or let RMail autogenerate one to decrypt email messages. Your recipients can also set their own decryption passwords.


Sometimes you take all the standard security measures to protect your content, only to find that the recipient later replies or forwards your email unencrypted, exposing your sensitive information. RMail offers a slew of content control features that will ensure your sensitive content remains protected even if it’s sent unencrypted or forwarded.
1. Redact+ - You can tag selected sensitive parts of an email by adding a carat sign (^), so that those parts are removed from the email body, which prevents recipients from replying or forwarding. It’s like erasing sensitive content from within an email or kill access to an attached document while at the recipient’s end. You can customize it to be viewed and redact access after one-view, a certain timeframe, or other criteria. This is part of RMail’s “protect-the-thread” revolution.
2. Disappearing Ink – To keep ultra-sensitive parts of messages private, use RMail’s Disappearing Ink to tag certain parts of an email message so that they disappear from within the email after delivery. You can set a timeframe to have the message disappear based on number of views, or time per view. Think of a remote-control way to “kill” certain content in email even after sending it.


3. Double Blind CC – You can remove the blind copy recipient reply-all risk. This is useful if you don’t want all the recipients to know who you are blind copying. With this feature, you can also remove potentially embarrassing moments when a BCC recipient deliberately or inadvertently replies to all.
Email is an indispensable part of our lives now. It’s critical for businesses to not become complacent when it comes to protecting data shared via emails, as it can cause severe damage. With the growing threat of email threats, BEC frauds, viruses, spam, phishing, identity theft, and ransomware attacks, businesses have an added responsibility to secure their business data and treat email security as a priority.
RMail is simple to use and protects your data at a fraction of a cost of what you currently spend. Try it to protect your emails for free!